
Understanding Physical Security Metrics
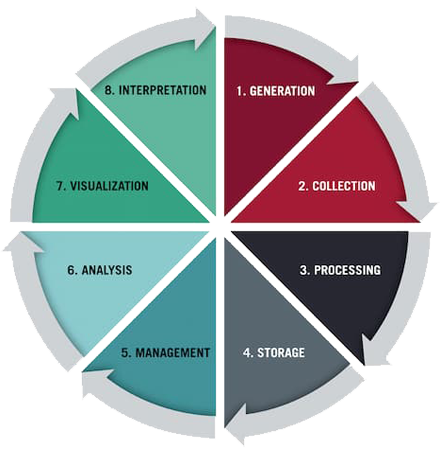
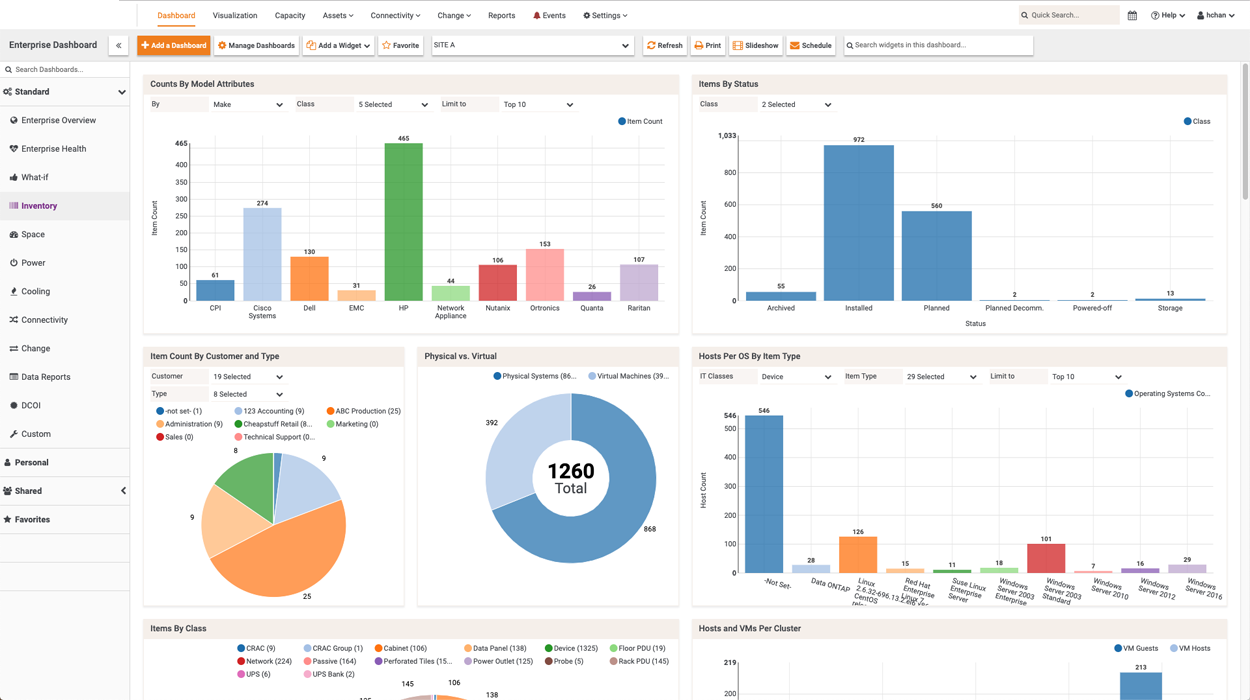
- Measuring Security Effectiveness Physical security metrics provide quantifiable data that enables organizations to assess the effectiveness of their security measures. By analyzing these metrics, vulnerabilities and areas for improvement can be identified, allowing for targeted strategies to enhance overall security posture.
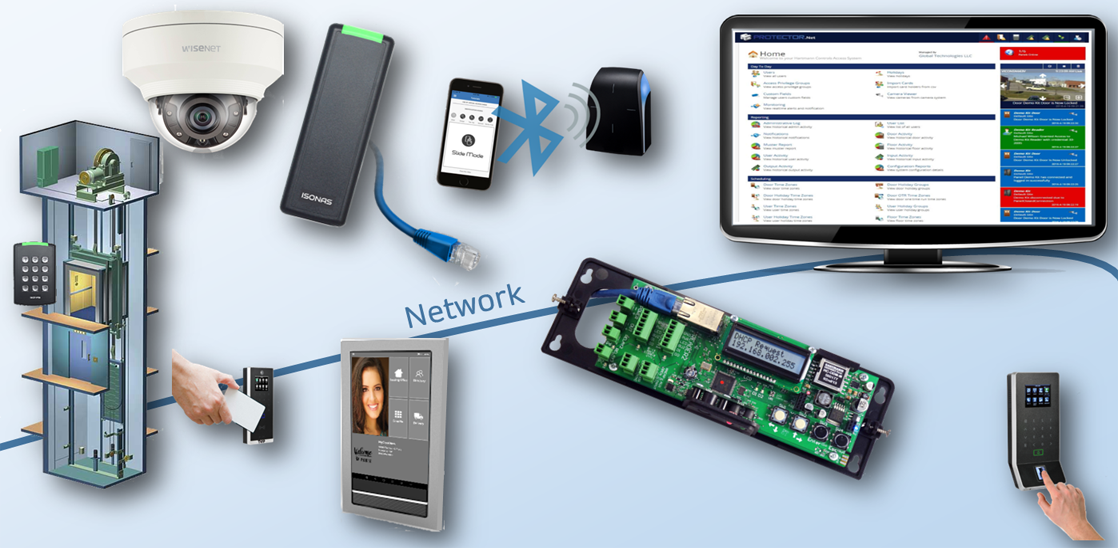
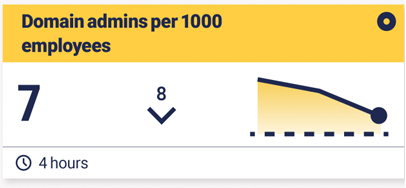
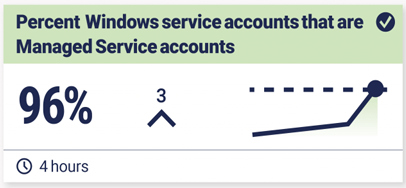
- Risk Assessment and Mitigation Tracking metrics related to access control, surveillance, and incident response empowers organizations to conduct comprehensive risk assessments. This data-driven approach facilitates the implementation of targeted mitigation strategies, effectively reducing potential security threats and vulnerabilities.
- Compliance and Regulatory Requirements Physical security metrics play a crucial role in demonstrating compliance with industry regulations and standards. By providing evidence of due diligence in safeguarding assets and personnel, organizations can meet regulatory requirements and maintain a strong security posture.